
Online Safety 101: How to Keep Cyber Snoopers at Bay

Have you ever paused to reflect on those emails from your bank urging you to update your information or the seemingly innocent act of connecting to your favorite coffee shop's Wi-Fi for a quick cup of joe? In the vast landscape of our digitally connected lives, have you ever entertained the thought of whether someone might be eavesdropping on your conversations?
In the contemporary world, where our daily routines intertwine seamlessly with digital communication, safeguarding the security and privacy of our online interactions has assumed a position of unparalleled significance. Alas, the challenge persists as cybercriminals continuously evolve, devising innovative methods to exploit vulnerabilities within our digital systems. Among these threats, the man-in-the-middle attack stands out as a particularly sophisticated and menacing technique, posing a substantial risk to the integrity of our digital security.
In this article, we explore the man-in-the-middle attack, unraveling its intricate workings, understanding its far-reaching implications, and, most importantly, arming ourselves with knowledge on how to shield against this pervasive cybercrime. Join us on this journey as we delve into the nuances of digital security and equip ourselves with the tools to navigate the ever-evolving landscape of cyber threats.
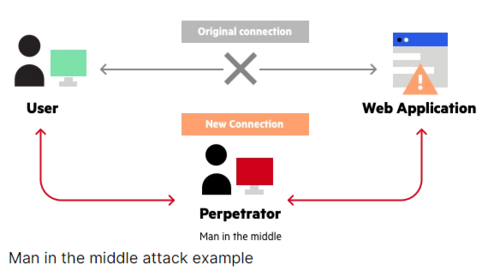
Source: Imperva.com
What is a Man-In-The-Middle Attack?
Imagine a scenario where your digital conversations aren't as private as you think; that's the unsettling reality of a man-in-the-middle (MITM) attack, a serious cybersecurity threat more pervasive than we might realize. In this digital battleground, an attacker sneaks into the communication channel between two unsuspecting parties, much like a sneaky postal worker sorting through your mail.
The term "man-in-the-middle" is fitting because, just like that rogue mailman, the attacker plants themselves right in the middle of the communication flow. It's akin to this mail mischief-maker intercepting your bank statement, jotting down your account details, and then sealing the envelope back up before it reaches your mailbox. The victim remains blissfully unaware of this intrusion.
So, why is this cyber maneuver so dangerous? Well, imagine the rogue mailman stealing not just your bank statement but also your login credentials, credit card numbers, and other personal details. That's what happens in an MITM attack. The attacker gains access to sensitive information, opening the door to identity theft, unauthorized fund transfers, and other malicious exploits.
What makes MITM attacks particularly treacherous is their stealthy nature. They can lurk undetected for long periods, silently pilfering information. It's like a silent invader setting up camp in your digital space without you even realizing it. Worse yet, these attacks can introduce malware onto your device, giving the attacker complete control over your system.
MITM attacks come in various shades, from the passive ones, where the attacker slyly intercepts user traffic, to the active ones, where the attacker actively manipulates or alters the data flow. It’s like different tactics in a cyber playbook – IP spoofing, DNS spoofing, HTTPS spoofing, and email spoofing, each with its own crafty strategy.

Source: ReadyTechGo.com
Interception
Have you ever gotten a sketchy message from an unknown number posing as your bank or an enticing email from a supposed unfamiliar angel promising a piece of his fortune? These seemingly harmless messages might just be the tip of the iceberg regarding a man-in-the-middle (MITM) attack, a favorite trick in the cyber criminal's playbook, where sensitive information is stolen from the unsuspecting victim.
So, what's the deal with interception, and how does it play into the whole MITM drama? Interception is like a digital sleight of hand with which the attacker slyly intercepts your online traffic before it reaches its intended destination. In the MITM attacks, the cyber trickster strategically positions themselves between two chit-chatting parties to either sneak a peek or slyly tweak the data passing between them.
The more straightforward and common form of MITM interception is where the attacker sets up a free Wi-Fi hotspot, maybe with a sneaky name like "CoffeeShop_FreeWiFi," and lures unsuspecting victims. Once connected, the attacker gets a backstage pass to all the victim's online data exchanges, kind of like a digital puppet master pulling the strings.
The attacker can spoof your IP and trick your computer into thinking it's hitting up a legitimate website when, in reality, it's a detour to the attacker's lair. Another move is DNS spoofing, where the attacker messes with your computer's GPS, sending it to the wrong digital address, aka their server, instead of the real deal. And who could forget HTTPS spoofing? This is like setting up a fake secure website, inviting victims to input their sensitive info, and then snatching it up like a digital pickpocket.
Email spoofing is another player in the MITM game. The attacker crafts an email that looks legit, maybe even mimicking a trustworthy source, to lull victims into a false sense of security. Once the victim bites, the attacker swoops in to nab the sensitive data. Here's the kicker: in all these cyber theatrics, the attacker stays incognito, a ghost in the machine, intercepting and manipulating data without the communicating parties having a clue. They might even drop malware on a targeted user's device, making themselves right at home.
Decryption
Alright, let's unravel the second act in the drama of a man-in-the-middle attack, which is decryption. Now that the digital trickster has nabbed the data sailing between two parties, it's time for the grand reveal. Decryption, in simple terms, is like translating a secret code back into something understandable.
In the wild landscape of a man-in-the-middle escapade, decryption is the secret sauce that turns the jumbled-up, encrypted data back into its original, readable form. Now, why is this a big deal? Well, it's the key to unlocking a treasure trove of sensitive info – think login credentials, financial details, and personally identifiable information (PII). The attacker unleashes this process to expose what was meant to be private and secure.
One classic thing the attacker does is known as the packet sniffer. A virtual detective captures and dissects the data zipping across the network. It's like intercepting letters and reading them before they reach the recipient. Sneaky, right? Then there's the brute-force attack, a cyber brute trying every password combination until it hits the jackpot. It's like trying every key in the bunch until one finally opens the door. Another trick up the attacker's sleeve is the rainbow table attack, which is a cheat sheet of pre-computed encrypted passwords, speeding up the process of finding the original password. It's the cyber equivalent of having a master key.
But why should we care about decryption? Well, if the attacker succeeds, they waltz right into sensitive information territory. This can lead to identity theft, fraud, and other malicious endeavors. Plus, decryption is like the golden ticket for installing malware on a targeted user's device, the cyber version of an uninvited guest overstaying their welcome.
Prevention
Now that we've uncovered the ins and outs of man-in-the-middle attacks and how these sneaky maneuvers go down let's arm you with the knowledge to steer clear of falling victim to them. Lucky for us, there are several effective methods to keep these digital tricksters at bay. Let's dive into some savvy ways to keep yourself in the clear:
1. Embrace the Power of VPNs:
Think of a Virtual Private Network (VPN) as your digital superhero cape. It encrypts all your internet traffic and guides it through its own secure servers. Even if an attacker tries to intercept your data, they'll just be staring at a wall of encryption. It's like sending your online messages in an unbreakable code.
.png)
Source: Markethive.com
2. HTTPS and SSL/TLS:
This dynamic duo of HTTPS and SSL/TLS transforms your internet communication into a secret language. When you visit a website using HTTPS, just like Markethive does, your browser locks arms with the website's server in a secure handshake. An attacker attempting to eavesdrop finds nothing but encrypted gibberish. It's like turning your online conversations into an encrypted treasure chest.
3. Safeguard with Email and DNS Security:
Email and DNS can be the Trojan horses of MITM attacks, but fear not! Strengthen your defenses with email security tools like SPF, DKIM, and DMARC to verify the legitimacy of your emails. For DNS, enlist the help of a secure resolver to ensure your DNS requests aren't being intercepted. It's like adding an extra layer of protection to your digital communication channels.
Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC) are email security tools that can help you protect your emails from spoofing, phishing, and spam. They work by verifying the sender’s identity and the integrity of the email content.
4. Double Down with Two-Factor Authentication (2FA):
Think of 2FA as having a bouncer at the entrance to your digital party. It requires a password and a second form of verification, like a code sent to your phone. This tag team ensures that only you get VIP access. It's like having a secret handshake for your online accounts.
5. Arm Yourself with Anti-virus Software:
Consider anti-virus software as your digital bodyguard. It scans, detects, and blocks potential threats, acting as a shield against MITM attacks. Keep it up-to-date to stay one step ahead of the cyber baddies.
6. Keep Software Updated:
Updating your software is like giving your digital fortress a fresh coat of paint. Hackers often exploit vulnerabilities in outdated software, so ensure your operating system, web browser, and other applications are rocking the latest security patches. It's like fortifying your defenses against unseen invaders.
It's essential you understand that by weaving these prevention methods into your digital routine, you significantly reduce the risk of becoming a victim of a man-in-the-middle attack. Remember, an ounce of prevention is worth a pound of cure. So, gear up, stay vigilant, and keep the online baddies at bay!
Detecting a Man-In-The-Middle Attack
Detecting a man-in-the-middle attack can be subtle, but it’s important to stay alert. The first sign something’s off will likely be a slowdown in internet or network speed. If you notice it taking longer than usual to load pages, watch out; you might be under attack. The next sign is a pop-up error message. These error messages can appear for several reasons, but if the error message says, “The security certificate presented by this website is not secure,” that’s a red flag. An improper security certificate is a definite sign that the website is not secure and may have been compromised.
Network Monitoring is essential in detecting a man-in-the-middle attack. Network monitoring tools come in various shapes and sizes. They keep track of network traffic, identify traffic patterns, and check for suspicious behavior. SSL Certificate Warnings are some of the most common ways web browsers detect a Man-in-the-Middle Attack.
When attempting to visit a website with an invalid certificate, the browser warns its user of its dangers, often citing the risk of middleman attacks. Suspicious Network Activity is another sign. If your network administrator or ISP has monitoring tools in place, unusual network activity can quickly raise a red flag. DNS Spoofing Detection Tools can help detect DNS hijacking and monitor suspicious activity on your network.
It's always best to have multiple lines of defense when trying to detect a man-in-the-middle attack. Using a combination of techniques and tools is key to recognizing suspicious activity before it's too late. Remember, prevention is always the best defense. Staying vigilant and using the preventive measures outlined in the previous section is vital.
Examples of Man-In-The-Middle Attacks
As you might have figured out by now, man-in-the-middle (MITM) attacks are pretty dangerous. They are used to steal sensitive information from various targets, including users of financial applications, e-commerce sites, and SaaS businesses. Such attacks can also gain entry into a secure network by installing malware on a user's device.
But let's dive deeper and look at some real-life instances of man-in-the-middle attacks that have occurred. In 2010, an Iranian hacker used a man-in-the-middle attack to access the Gmail accounts of several high-profile individuals, including US government officials and journalists. The attacker created a fraudulent security certificate for Google services, which allowed them to intercept email communication.
DigiNotar, a Dutch certificate authority that the hacker compromised, issued the security certificate. The hacker bypassed the HTTPS encryption that usually protects the communication between a user and a website. The hacker also used a technique called DNS spoofing, which involves changing the DNS records of a domain name to point to a malicious server. This way, the hacker could redirect the users to a fake Google website that looked identical to the real one but was under the hacker’s control.
In 2011, at a Black Hat conference, a researcher named Nicholas Percoco and his colleague Christian Papathanasiou showed how easy it was to run a man-in-the-middle attack on mobile devices running iOS and Android. The attack involved intercepting data packets between a mobile device and a wireless access point using a tool called SSLstrip.
SSLstrip is a tool that can downgrade HTTPS connections to HTTP connections and strip away the encryption that normally protects the communication between a user and a website. The tool can also modify the content of the web pages that the user sees, such as replacing the padlock icon with a fake one or inserting malicious links or scripts.
The researchers demonstrated how they could use SSLstrip to hijack a user’s Facebook session, steal their login credentials, and post messages on their behalf. They also showed how to intercept a user’s email communication, read their messages, and send spoofed emails. They also revealed how to access a user’s online banking account, view their balance, and transfer money to another account.
One of the most widespread man-in-the-middle attacks in recent times is the "Superfish" incident. Lenovo shipped its laptops with adware called "Superfish," designed to serve targeted ads to users. However, Superfish was designed to intercept HTTPS traffic, leaving users vulnerable to MITM attacks.
Another example of a widespread MITM attack is the WannaCry ransomware attack that took place in 2017. The WannaCry ransomware was propagated via a vulnerability in Windows systems and encrypted users' files, demanding a ransom for decryption. This sophisticated ransomware attack attacked several government agencies, businesses, and individuals worldwide.
While most man-in-the-middle attacks aim to steal user data, some use MITM attacks to target companies and individuals. For instance, during the Syrian civil war, the SEA (Syrian Electronic Army) carried out a targeted MITM attack against the Associated Press (AP) Twitter account. The SEA used the account to post fake news about an explosion at the White House, causing a significant drop in the stock market. While man-in-the-middle attacks might not be new, the stakes are increasing with new technologies such as Artificial Intelligence. So, it's crucial that you stay informed of such attacks and take the necessary precautions to protect your data.

Source: Cyber Security News
Security analysts discovered one recent incident of an MITM attack in April 2023. The attack targeted Wi-Fi networks and could bypass their security mechanisms. The attacker operated by imitating the genuine access point and transmitting a forged Internet Control Message Protocol (ICMP) to redirect the message to a targeted supplier. ICMP is a protocol used to send error messages and other information between network devices.
A redirect message is an ICMP message that tells a device to use a different route to reach a destination. By sending a forged redirect message, the attacker could trick the device into sending its traffic through a malicious router, where the attacker could intercept and modify it. This way, the attacker could hijack any device's traffic connected to the Wi-Fi network and perform various malicious activities, such as stealing passwords, injecting ads, or redirecting users to phishing websites.
Conclusion
So, we know these attacks are dangerous and can happen to anyone, anywhere, at any time. From intercepting personal information to potentially installing malware, cybercriminals will stop at nothing to get what they want, which is why it's so important to be aware of the risks posed by man-in-the-middle attacks.
We've gone over a few key steps to prevent becoming a victim, like using a VPN, HTTPS, SSL/TLS, email and DNS security, and two-factor authentication. It's also essential to keep your software up-to-date and be aware of suspicious network activity. But even with these precautions, it's not always possible to avoid a man-in-the-middle attack, so it's important to know how to detect one if it does happen.
Whether it's noticing strange SSL certificate warnings or monitoring network activity, early detection can be the difference between a minor inconvenience and a major data breach. And while it's easy to feel overwhelmed by the thought of cybercriminals lurking around every corner, being aware of the risks posed by man-in-the-middle attacks is the first step toward protecting yourself.
Remember, attacks like these can happen to anyone. Still, you can minimize your risk and stay safe in an increasingly dangerous digital world by remaining vigilant and taking the necessary precautions. So, whether you're shopping online, checking your bank account, or browsing the web, remember to stay alert, stay safe, and watch for those pesky man-in-the-middle attacks. After all, when it comes to online security, a little awareness can go a long way to save you from disaster.

David Http://markethive.com/david-ogden



.png)
